Go Phish – Protect Yourself and Your Business from Phishing Scams
May 25th, 2017 | 4 min. read


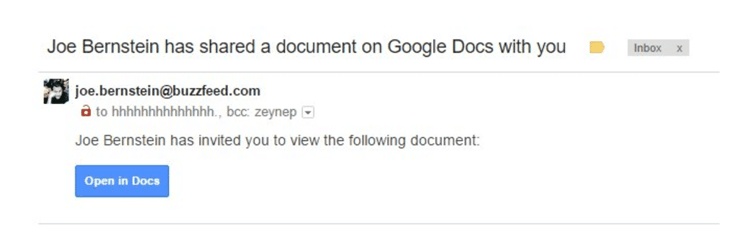
Phishing scams have been with us since the dawn of the Internet. They'll stay with us until we all learn to stop falling for these scams (so, basically, they'll be with us forever).
Our primary focus as your IT services partner is to secure the perimeter of your business – we keep the bad stuff out as much as possible. Even with up-to-date antivirus patches, the best firewalls, and constantly evolving security methods as best practices change; there's no such thing as a 100%, impervious network security.
Some phishing scam attacks can make it through to your (and your employees') inboxes.
Once that happens, it's up to you to be educated enough to not fall for a phishing scam. Unfortunately, they're not all as obvious as Nigerians looking to rain money upon us in return for our bank account information. And, seriously, who falls for that!?!?!?
Like in poker though, there are some “tells” for identifying a phishing scam.
General security tips:
- Don't enter personal financial information over public WI-Fi, even if secured.
- Don't assume that an email from a friend or known associate is legitimate – if it looks out of character for them to send to you, they could have clicked on a phishing email themselves!
- Be wary of non-HTTPS sites. The “s” stands for “secure” and is the new standard for sites. This isn't foolproof as some phishers have managed to forge security icons.
- Update your Web browser.
- And the biggest rule of all: Do not enter any personal information, usernames, or passwords in response to an email or on a website that is linked to in an email.
Here are some of those “tells” I mentioned:
- Watch for urgent calls to action, especially if they request your personal information. For example: “You must act now to verify your account.” Often these will be tied to seasonal trends, such as tax season.
- Look for grammar or spelling mistakes, but don’t rely on them to give away phishing attempts.
- If you think a message looks odd in any way, do not click on any links or attachments in the message. Watch out for emails that do not match the normal writing style of the sender or are strangely brief. When in doubt, contact the person it came from in some other manner (e.g., call them using a number you know is legitimate.)
- ·If you hold your mouse pointer over a link without clicking (called a mouse-over), you can preview the URL it leads to by looking in the bottom left corner of your browser window. If the URL looks suspicious or unexpected, it’s most likely a phishing attempt.
- Pay attention to the URL as well, a legitimate-looking email and URL could be off by a single letter, persuading you to click if you're in a rush or simply not paying close attention.
And if you are a victim, having a good backup strategy in place is a great way to limit any damage clicking on a malicious link can cause either you personally or your business.
For more information about phishing, here are some useful resources:
- smartcomputing.unlv.edu/phishing
- https://www.consumer.ftc.gov/articles/0003-phishing
- http://www.phishing.org/10-ways-to-avoid-phishing-scams
Ready to prevent criminals from phishing in your company pool? We can do a network assessment to identify areas of weakness.
Mo is the resident IT go-to lady at AIS. She has traveled the world, run a marathon, is a self-proclaimed crossword champion, and can do ventriloquism. She has an uncanny memory ....down to the detail. She has completed 4 half marathons and hates running. In her free time, she likes to spend time with her 7 siblings and 20 nieces and nephews.
Topics:



